Simple Column Transposition
Cipher that interchanges lines of the plaintext
The first 10 lines of the grid are shown
python transpostion.py --encrypt --message 'Hello this is a test. Please enter your text here' --key 'Cipher' --alphabet '' --case-sensitive --replace-char ''
Background
In cryptography, transposition is a cipher where the order of the letters is changed instead of replacing the letters with other symbols as in the substitution cipher.
Description and operations
Column transposition uses a rectangular arrangement (also called a matrix or grid), consisting of several rows (as many as are necessary to enter the plain text). The number of columns is given by the length of the key (also called keyword). The plaintext is then entered into the grid line by line. Afterwards 2 header lines are added: The first one contains the keyword, the second one consists of the numbers, which are obtained by arranging the characters in the keyword alphabetically (permutation). Then the columns are read in the order of the numbers of the permutation. In this implementation the permutation from the keyword is determined as follows: All characters are identified by their ASCII value. Thus, a distinction is made between upper and lower case letters. All printable characters [ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789ÄÖÜäööü .,:;!?()-+*/[]{}@_><#~=\"&%$§] are possible as the alphabet for the keyword. A character can also occur several times (the first of these same characters is taken first, then the next and so on). Here are a few examples how the permutation is calculated:
Example: Key Permutation
AB 12
aB 21
SCHELL 613245
SCHell 312456
ellSCH 456312 As an example we encrypt the message "Hello this is an example" with the keyword 'Cipher'.
1. Create the grid
2. Fill the grid
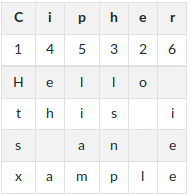
3. Enter table headers and permutation
4. Read out by column
Security
Since a transposition does not influence the frequency of the individual symbols, it can be easily identified by a frequency analysis whether this encryption method is used: So if the encrypted text has a frequency distribution that is very similar to normal plaintext it is most likely a transposition. This detects the cipher type, but not yet the key (permutation). For multiple consecutive transpositions with long random keys, the cryptoanalysis is not easy even with today's methods.
References
● Transposition cipher: https://en.wikipedia.org/wiki/Transposition_cipher
About the code
In this plugin you can control the encryption process in two ways:
- via the GUI
- via the command line arguments for the Python program
The Python code is executed purely locally in your browser without the need to install a Python development environment, but also without, that the Python code must be executed somewhere in the cloud. The following parameters can be changed via the GUI:
- the text to be entered
- whether to encrypt or decrypt the entered text
- the key
- the alphabet used for the message and the passphrase
- whether the output text should be output in blocks of five
- whether spaces should be filtered out
- whether spaces should be replaced with another character
These GUI parameters are passed to the script on the command line. Changes in the GUI change the respective command-line parameters.
The code is an implementation of the simple transposition encryption in Python. Depending on whether the input is to be decrypted or encrypted, the corresponding function is executed. In case of the encryption, the characters are distributed to columns. Then the key is sorted alphabetically and a number is assigned to each character in the key. This number corresponds to the alphabetical order. Finally, the columns are joined together based on their order. In the case of decryption, the number of rows and the difference are calculated first. This difference corresponds to the placeholders in the last row. Then an empty matrix is created. The number of columns in the matrix corresponds to the length of the key. As in the encryption, the key sorted alphabetically. The matrix is filled based on the alphabetical order of the key. For each row in the matrix, each column is iterated through. For each iteration, characters from one row are joined together. Thus you get the decrypted message.
About the editor
The editor available on this page was implemented with CodeMirror [1]. CodeMirror is a versatile text editor that is implemented in JavaScript for the Browser was implemented. CodeMirror has a number of add-ons for different of programming languages. Pyodide [2] is used to execute the Python code.
Pyodide brings the Python runtime environment via WebAssembly into the browser, together with NumPy, Pandas, Matplotlib, parts of SciPy and NetworkX. In the editor there is now an interpreter for Python 3.x . You can see which exact Python version is used by Pyodide – by adding the following statement to the code: print(sys.version).