Password Meter
Evaluates the strength of an entered password locallyHow secure your password is classified by different evaluation methods, you can check here purely locally. Your entries are neither transferred nor stored. For a good password, the length is most important.
Your browser does not support all the technologies used. If this tool does not work for you, please update your browser. If the plugin still fails to run as expected, please write us a message via the contact form.
Length: 0
For very long passwords, the rating may take longer and your browser may not respond immediately.
Dictionaries
| # | Name | Words | 🗑 |
|---|
These dictionaries are only used by the method "Stutz' PS". A dictionary file must contain one word per line.
Rating
KeePass:
0% (0 Bits)
Mozilla:
0%
PGP:
0% (0 Bits)
zxcvbn:
0%
Stutz' PS:
0% (0 Bits)
Total:
0%
The color of the progress bar indicates the password strength: red = very weak, yellow = medium and green = very strong.
Details
Time to crack (online):
-
Time to crack (offline):
-
Sequences found:
-
Notice:
-
Suggestions for improvement:
-
When estimating the online cracktime, it is assumed that an attacker has no access restrictions, the server responds immediately and does not wait even after a certain number of attempts.
For offline cracktime, we assume that the attacker uses a fast PC and knows the password hash, and that the passwords have been hashed using a slow hashing method. If a fast hashing method was used instead, the time required will be significantly shorter.
For offline cracktime, we assume that the attacker uses a fast PC and knows the password hash, and that the passwords have been hashed using a slow hashing method. If a fast hashing method was used instead, the time required will be significantly shorter.
Average cracktime:
-
| Pattern | Entropy | Type |
|---|---|---|
| - | - | - |
How to use
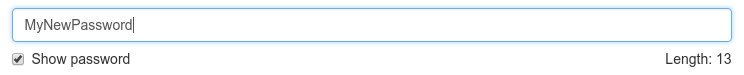 To have a password evaluated, enter it in the input field. As a result, the quality of the password will be estimated by various methods. The evaluations of the different methods will be displayed in the form of a colored progress bar. The total ranking is also displayed in the form of a colored progress bar.
To have a password evaluated, enter it in the input field. As a result, the quality of the password will be estimated by various methods. The evaluations of the different methods will be displayed in the form of a colored progress bar. The total ranking is also displayed in the form of a colored progress bar. 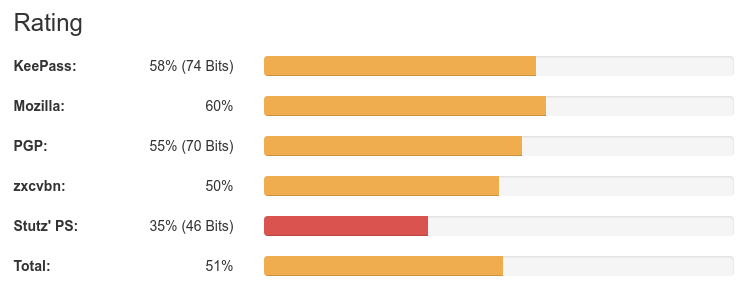 The color of the bar reflects the quality: red means "very weak", yellow means "medium", and green means "very good". The exact quality and possibly also the entropy values of the password are output as percentages next to the bars.
The color of the bar reflects the quality: red means "very weak", yellow means "medium", and green means "very good". The exact quality and possibly also the entropy values of the password are output as percentages next to the bars. 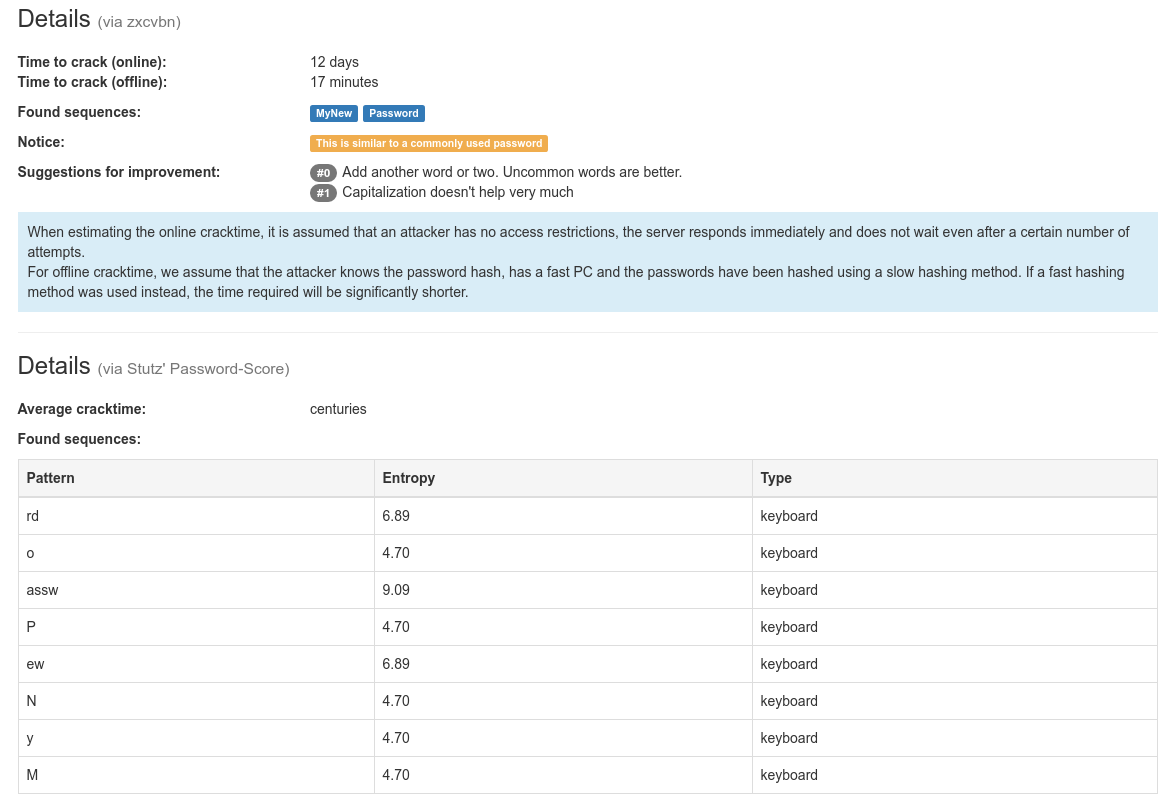 The methods "zxcvbn" and "Stutz' PS" provide more information about the password, such as found sequences and the estimated cracking time. In addition, zxcvbn also shows suggestions to improve passwords labeled "weak".
The methods "zxcvbn" and "Stutz' PS" provide more information about the password, such as found sequences and the estimated cracking time. In addition, zxcvbn also shows suggestions to improve passwords labeled "weak".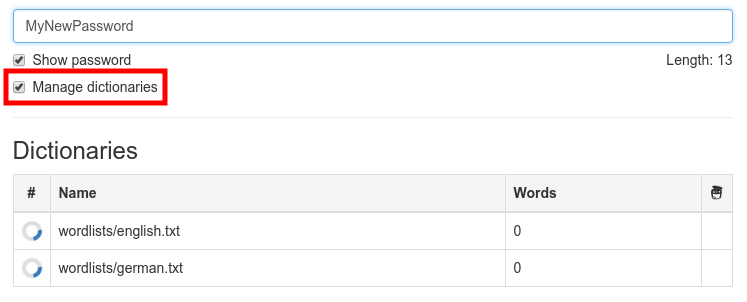 Stutz' PS offers the ability to have the password checked for crackability through a dictionary attack. For this, mark the checkbox at "Manage dictionaries". After that, a new area will be shown and two standard dictionaries will be downloaded. These contain the most common words from the English and German languages.
Stutz' PS offers the ability to have the password checked for crackability through a dictionary attack. For this, mark the checkbox at "Manage dictionaries". After that, a new area will be shown and two standard dictionaries will be downloaded. These contain the most common words from the English and German languages. 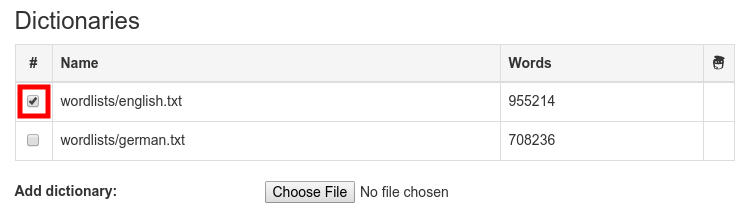 Once the dictionaries have finished downloading, they can be used by marking them with a tick.
Once the dictionaries have finished downloading, they can be used by marking them with a tick.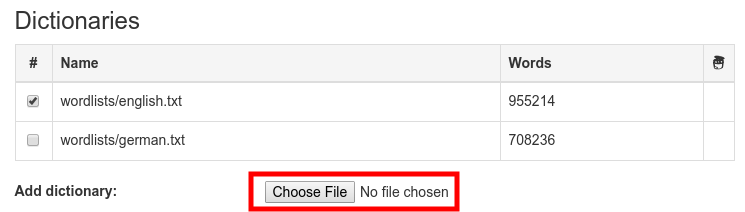 You can include your own custom dictionaries by clicking "Choose File" and selecting a dictionary file from your hard disk.
You can include your own custom dictionaries by clicking "Choose File" and selecting a dictionary file from your hard disk. 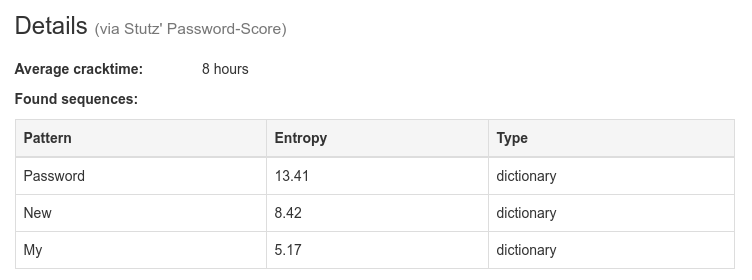 The dictionary then is loaded into the memory of your browser and is used by the method "Stutz' PS". The other rating methods don't use dictionaries.
The dictionary then is loaded into the memory of your browser and is used by the method "Stutz' PS". The other rating methods don't use dictionaries.  A dictionary file always contains one word per line and can not be larger than the available memory in your browser. A word is always the string of a line up to the first occurrence of a space.
A dictionary file always contains one word per line and can not be larger than the available memory in your browser. A word is always the string of a line up to the first occurrence of a space.If the plugin does not work for you as described here, please update your browser. If the plugin still does not work as expected, please write us a message via the contact form.
Further information
By now we know: More important than the use of different character types (special characters, capital letters and numbers) is the length of the password. Therefore, make sure that your password has more than 12 characters, is random and contains no personal information. Adding a few special characters, capital letters and numbers does not hurt either. But make sure that you do not use them instead of letters or only at the end of the password. This 11 minutes YouTube video gives a more detailed insight.
Usually an attacker only has the possibility to try out common passwords, often used strings, words from a dictionary, and varying characters (for example, a "3" instead of an "e"). If he also has personal information about you, he will also include data such as your date of birth. For a good demonstration, check out this 20 minutes YouTube video.
Yes. Because in case that one of your passwords gets into the wrong hands, the damage should be minimal: If an attacker finds out the password of your facebook account, he should not be able to buy things at Amazon on your invoice.
Ideally, of course, in your head. If you still wish to write down your password, be sure to keep it in a secure place (such as a safe). A good alternative are encrypted password files and password managers such as KeePass.
The upper three methods are from the applications KeePass, Mozilla Firefox and PGP. Each of them has an integrated password quality meter. The methods "zxcvbn" and "Stutz' Password-Score" have both been inspired by this article (Dan Wheeler, 2012).
Most methods evaluate the quality of a password based on entropy. This approach is followed by e.g. the applications KeePass and PGP. It is assumed that a quality of 100% corresponds to an entropy of 128 bits. The method "Stutz' Password-Score" uses a custom function to map the entropy to a percentage value. In the Mozilla method, the available characters are divided into groups of characters, which are then evaluated differently (for example, special characters and lowercase letters). The methods "zxcvbn" and "Stutz' Password-Score" additionally test the password for repetitive characters, keyboard sequences, and words that appear in a dictionary. The rating of the various methods usually lead to different results.
Please note that this tool is only an indication and that a good rating does not guarantee an unbreakable password. That the 5 methods give different results is normal.